Generate Microsoft Lync Private Key
- Generate Microsoft Lync Private Key Code
- Install Microsoft Lync
- Microsoft Lync Phone Setup
- Generate Microsoft Lync Private Keys
Topic Last Modified: 2013-11-07
Important
When you run the Certificate Wizard, ensure that you are logged in using an account that is a member of a group that has been assigned the appropriate permissions for the type of certificate template you will use. By default, a Lync Server 2013 certificate request will use the Web Server certificate template. If you use an account that is a member of the RTCUniversalServerAdmins group to request a certificate using this template, verify that the group has been assigned the Enroll permissions required to use that template.
Certificates for Microsoft Lync Microsoft Lync is a new tool for enterprises communication. Lync 2013 Frontal and Lync 2013 Edge), you must create an exportable private key while generating your CSR. The Lync Server Access Edge on Local Computer. For more information, review the System Event Log. If this is a non-Microsoft.
A single certificate is required on the internal interface of each Edge Server. Certificates for the internal interface can be issued by an internal enterprise certification authority (CA) or a public CA. If your organization has an internal CA deployed you can save on the expense of using public certificates by using the internal CA to issue the certificate for the internal interface. You can use an internal Windows Server 2008 CA or Windows Server 2008 R2 CA to create these certificates.
To export the certificate with the private key for Edge Servers in a pool Log on as a member of the Administrators group to the same Edge Server on which you imported the certificate. Click Start, click Run, and type MMC. How can I find the private key for my SSL certificate. If you just got an issued SSL certificate and are having a hard time finding the corresponding private key, this article can help you to find that one and only key for your certificate. Feb 14, 2014 To generate a certificate signing request on the computer where the certificate and private key will be assigned, you do the following: Creating a certificate signing request Open the Microsoft Management Console (MMC) and add the Certificates snap-in and select Computers, then expand Personal.
For details about this and other certificate requirements, see Certificate requirements for external user access in Lync Server 2013.
To set up certificates on the internal edge interface at a site, use the procedures in this section to do the following:
Download the CA certification chain for the internal interface to each Edge Server.
Import the CA certification chain for the internal interface, on each Edge Server.
Create the certificate request for the internal interface, on one Edge Server, called the first Edge Server.
Import the certificate for the internal interface on the first Edge Server.
Import the certificate on the other Edge Servers at this site (or deployed behind this load balancer).
Assign the certificate for the internal interface of every Edge Server.
If you have more than one site with Edge Servers (that is, a multiple-site edge topology), or separate sets of Edge Servers deployed behind different load balancers, you need to follow these steps for each site that has Edge Servers, and for each set of Edge Servers deployed behind a different load balancer.
Note
The steps for procedures in this section are based on using a Windows Server 2008 CA, Windows Server 2008 R2 CA, Windows Server 2012 CA, or Windows Server 2012 R2 CA to create a certificate for each Edge Server. For step-by-step guidance for any other CA, consult the documentation for that CA. By default, all authenticated users have the appropriate user rights to request certificates.
The procedures in this section are based on creating certificate requests on the Edge Server as part of the Edge Server deployment process. It is possible to create certificate requests using the Front End Server. You can do this to complete the certificate request early in the planning and deployment process, before you start deployment of the Edge Servers. To do this, you must ensure that the certificate you request is defined with an exportable private key.
The procedures in this section describe using a .cer and a .p7b file for the certificate. If you use a different type of file, modify these procedures as appropriate.
To download the CA certification chain for the internal interface using certsrv Web site
Log on to an Lync Server 2013 server in the internal network (that is, not the Edge Server) as a member of the Administrators group.
Run the following command at a command prompt by clicking Start, clicking Run, and then typing the following:
For example:
Note
If you are using a Windows Server 2008 or Windows Server 2008 R2 enterprise CA, you must use https, not http.
On the issuing CA’s certsrv web page, under Select a task, click Download a CA certificate, certificate chain, or CRL.
Under Download a CA Certificate, Certificate Chain, or CRL, click Download CA certificate chain.
In the File Download dialog box, click Save.
Save the .p7b file to the hard disk drive on the server, and then copy it to a folder on each Edge Server.
Note
The .p7b file contains all of the certificates that are in the certification path. To view the certification path, open the server certificate and click the certification path.
To export the CA certification chain for the internal interface using MMC
You can export the CA root certificate from any domain joined machine using the Microsoft Management Console (MMC). Click Start, click Run, and then type MMC.
In the MMC console, click File, click Add/Remove.
From the Add or Remove Snap-ins dialog list, select Certificates, then click Add. When prompted, select Computer Account. On the Select Computer dialog, select Local Computer. Click Finish. Click OK.
Expand Certificates (Local Computer). Expand Trusted Root Certification Authorities, select Certificates.
Click the root certificate issued by your CA. Right click the certificate, select All Tasks, select Export. The Certificate Export Wizard will open.
In the Certificate Export Wizard, click Next.
On the Export File Format dialog, select a format to export to. We recommend the Cryptographic Message Syntax Standard – PKCS #7 Certificates (.P7B). If you select the Cryptographic Message Syntax Standard – PKCS #7 Certificates (.P7B), select the Include all certificates in the certification path if possible checkbox to export the certificate chain, including the root CA certificate and any Intermediate CA certificates. Click Next.
On the File to Export dialog in the file name entry, type a path and file name (default extension is .p7b) for the exported certificate. Optionally, click Browse, locate a directory to place the exported certificate in and provide a name for the exported certificate. Click Save. Click Next.
Review the summary of actions, and click Finish to complete the export of the certificate. Click OK to confirm the successful export.
To import the CA certification chain for the internal interface
On each Edge Server, open the Microsoft Management Console (MMC) by clicking Start, clicking Run, typing mmc in the Open box, and then clicking OK.
On the File menu, click Add/Remove Snap-in, and then click Add.
In the Add Standalone Snap-ins box, click Certificates, and then click Add.
In the Certificate snap-in dialog box, click Computer account, and then click Next.
In the Select Computer dialog box, ensure that the Local computer: (the computer this console is running on) check box is selected, and then click Finish.
Click Close, and then click OK.
In the console tree, expand Certificates (Local Computer), right-click Trusted Root Certification Authorities, point to All Tasks, and then click Import.
In the wizard, in File to Import, specify the file name of the certificate (that is, the name of that you specified when you downloaded the CA certification chain for the internal interface in the previous procedure).
Repeat this procedure on each Edge Server.
To create the certificate request for the internal interface
On one of the Edge Servers, start the Deployment Wizard, and next to Step 3: Request, Install, or Assign Certificates, click Run.
Note
If you have multiple Edge Servers in one location in a pool, you can run the Certificate Wizard on any one of the Edge Servers.
After you run Step 3 the first time, the button changes to Run again, and a green check mark that indicates successful completion of the task is not displayed until all require certificates have been requested, installed, and assigned.On the Available Certificate Tasks page, click Create a new certificate request.
On the Certificate Request page, click Next.
On the Delayed or Immediate Requests page, click Prepare the request now, but send it later.
On the Certificate Request File page, type the full path and file name to which the request is to be saved (for example, c:cert_internal_edge.cer).
On the Specify Alternate Certificate Template page, to use a template other than the default WebServer template, select the Use alternative certificate template for the selected Certificate Authority check box.
On the Name and Security Settings page, do the following:
In Friendly name, type a display name for the certificate (for example, Internal Edge).
In Bit length, specify the bit length (typically, the default of 2048).
Note
Higher bit lengths offer more security, but they have a negative impact on speed.
If the certificate needs to be exportable, select the Mark certificate private key as exportable check box.
On the Organization Information page, type the name for the organization and the organizational unit (OU) (for example, a division or department).
On the Geographical Information page, specify the location information.
On the Subject Name/Subject Alternate Names page, the information to be automatically populated by the wizard is displayed.
On the Configure Additional Subject Alternate Names page, specify any additional subject alternative names that are required.
On the Request Summary page, review the certificate information that is going to be used to generate the request.
After the commands complete, do the following:
To view the log for the certificate request, click View Log.
To complete the certificate request, click Next.
On the Certificate Request File page, do the following:
To view the generated certificate signing request (CSR) file, click View.
To close the wizard, click Finish.
Submit this file to your CA (by email or other method supported by your organization for your enterprise CA) and, when you receive the response file, copy the new certificate to this computer so that it is available for import.
Generate Microsoft Lync Private Key Code
To import the certificate for the internal interface
Log on to the Edge Server on which you created the certificate request as a member of the local Administrators group.
In the Deployment Wizard, next to Step 3: Request, Install, or Assign Certificates, click Run again.
After you run Step 3 the first time, the button changes to Run again, but a green check mark (indicating successful completion of the task) is not displayed until all require certificates have been requested, installed, and assigned.
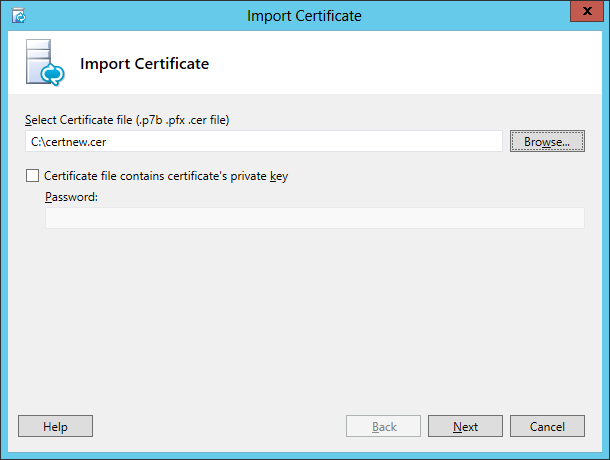
On the Available Certificate Tasks page, click Import a certificate from a .P7b, .pfx or .cer file.
On the Import Certificate page, type the full path and file name of the certificate that you requested and received for the internal interface of this Edge Server (or, click Browse to locate and select the file).
If you are importing certificates for other members of the pool a certificate containing a private key, select the Certificate file contains certifcate’s private key check box and specify the password.
To export the certificate with the private key for Edge Servers in a pool
Log on as a member of the Administrators group to the same Edge Server on which you imported the certificate.
Click Start, click Run, and type MMC.
From the MMC console, click File, click Add/Remove Snap-in.
From Add or Remove Snap-ins page, click Certificates, click Add.
In the Certificates snap-in dialog, select Computer account. Click Next. In Select Computer, select Local computer: (the computer this console is running on). Click Finish. Click OK to complete configuration of the MMC console.
Double-click Certificates (Local Computer) to expand the certificate stores. Double-click Personal, then double-click Certificates.
Important
If there are no certificates in the Certificates Personal store for the local computer, there is no private key associated with the certificate that was imported. Review the request and import steps. If the problem persists, contact your certification authority administrator or provider.
In the Certificates Personal store for the local computer, right-click the certificate that you are exporting. Click All Tasks, click Export.
In the Certificate Export Wizard, click Next. Select Yes, export the private key. Click Next.
Note
If the selection Yes, export the private key is not available, the private key associated with this certificate was not marked for export. You will need to request the certificate again, ensuring that the certificate is marked to allow for the export of the private key before you can continue with the export. Contact your certification authority administrator or provider.
On the Export File Formats dialog, select Personal Information Exchange – PKCS#12 (.PFX) and then select the following:
Include all certificates in the certification path if possible
Export all extended properties
Warning
When exporting the certificate from an Edge server, do not select Delete the private key if the export is successful. Selecting this option will require that you import the certificate and the private key to this Edge server.
Click Next to continue.
If you want to assign password to protect the private key, type a password for the private key. Re-enter the password to confirm. Click Next.
Type a path and file name for the exported certificate, using a file extension of .pfx. The path must either be accessible to all other Edge servers in the pool or available to transport by means of removable media - for example, a USB flash drive. Click Next.
Review the summary on the Completing the Certificate Export Wizard dialog. Click Finish.
Click OK in the successful export dialog.
Import the exported certificate file to the other Edge servers following the steps outlined in the Set up certificates for the external edge interface for Lync Server 2013 procedures.
Install Microsoft Lync
Microsoft Lync Phone Setup
To assign the internal certificate on the Edge Servers
Generate Microsoft Lync Private Keys
On each Edge Server, in the Deployment Wizard, next to Step 3: Request, Install, or Assign Certificates, click Run again.
On the Available Certificate Tasks page, click Assign an existing certificate.
On the Certificate Assignment page, select Edge Internal in the list.
On the Certificate Store page, select the certificate that you imported for the internal edge (from the previous procedure).
On the Certificate Assignment Summary page, review your settings, and then click Next to assign the certificates.
On the wizard completion page, click Finish.
After using this procedure to assign the internal edge certificate, open the Certificate snap-in on each server, expand Certificates (Local computer), expand Personal, click Certificates, and then verify in the details pane that the internal edge certificate is listed.
If your deployment includes multiple Edge Servers, repeat this procedure for each Edge Server.